Information Governance (IG) encompasses sets of multi‐disciplinary structures, policies, procedures, processes and controls implemented to manage records and information at an enterprise level, supporting an organization's immediate and future regulatory, legal, risk, environmental and operational requirements.
Definitions of IG go much further than traditional Records and Information Management (RIM) in order to address all phases of the records and information life cycle. Records management deals with the creation, retention and storage and disposition of records. A record can either be a physical tangible object, digital information such as a database, application data, and e‐mail. The lifecycle was historically viewed as the point of creation to the eventual disposal of a record. As data generation has exploded in recent decades, and regulations and compliance issues increased, traditional records management has failed to keep pace. A more comprehensive platform for managing records and information is necessary to address all phases of the lifecycle ‐ this has led to the advent of IG.
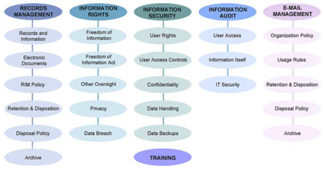
IG goes beyond retention and disposition to include overall information management rights, security, audit and e‐mail management. The table below is the BST Information Governance model with a brief description of each component.
BST Information Governance Model
Click to enlarge
RECORDS MANAGEMENT
Records and Information: is all forms of records and information registered in either temporary or permanent form so that it can be retrieved, reproduced, or preserved
Electronic Documents: is any electronic media content that is intended to be used in either an electronic form or as printed output
RIM Policy (Records and Information): is policy that aligns with an organization’s environment, strategic direction, policy framework, and records and information keeping. RIM policy should reflect current business and legal needs including endorsement by an organization’s senior executives. RIM Policy should:
-
be implemented and communicated regularly across the whole organization;
-
cover all systems that contain records and information;
-
cover all practices associated with records and information;
-
be linked to related business policies and programs;
-
be supported by sets of procedures, guidance, and tools for records and information management;
-
be enabled to be assessment compliance monitored; and
-
be assessed regularly.
Having a RIM policy provides key benefits including:
-
communication to all organization staff of the organization’s commitment to records management, and staff recordkeeping responsibilities;
-
provides the directive to ensure that the evidentiary, accountability and regulatory requirements of the organization are met;
-
promotes a holistic culture of good recordkeeping practice;
-
increases the probability of organization staff complying with good recordkeeping practice;
-
decreases the level of risk associated with recordkeeping practices;
-
enhances efficiency of business processes, practices and service delivery; and
-
encourages ethical behavior.
Retention and Disposition
-
Retention: is how records and information are stored for a given period of time in an organization’s document management policies. The information on critical documents must be protected for certain amounts of time. Retention periods for various documents are dictated by the needs of the organization and are measured up against what applicable laws and regulations require.
-
Disposition: is a critical element of records and information management and is the final operational action taken in the records and information lifecycle. Disposition includes the destruction of records and information or the transfer to another entity (most commonly an Archives) for permanent preservation. An organization’s records and information disposition program should provide approved routine procedures to dispose or transfer records and information that is no longer needed by the organization for current business.
Disposal Policy: is policy regarding the destruction or transfer of records and information. On some occasions, the disposal may be to transfer records and information to another State or Federal agency. Proper authorization prior to proceeding with disposal is usually needed. Disposal of records and information should occur routinely in accordance an organization’s records and information management policy.
Archive: is records and information that can be expected to be kept permanently and as closely as possible to its original form. Archival records and information can be "expected" to retain permanently its original characteristics. Permanent records and information determined to be of sufficient additional historical, or of continuing or enduring value, warrants conservation and preservation in an archival facility.
INFORMATION RIGHTS
Freedom of Information: is a legal reference to a citizen's right to access information that is held by various organizations. In many countries, this freedom is supported as a constitutional right.
Freedom of Information Act: is law that gives people the right to access information from the federal government.
Other Oversight: is oversight with the watchful care, management or supervision by a higher entity such as the government, laws, stakeholders, etc.
Privacy: is the relationship between collection and dissemination of records and information and the expectation of privacy, and the legal and political issues surrounding records and information. Privacy concerns can exist wherever personally identifiable records and information is collected and stored – on paper or in digital form. Improper or nonexistent disclosure control can be a root cause of privacy issues. Records and information privacy issues arise in response to information from a wide range of sources including, healthcare records, criminal justice investigations and proceedings, financial institutions and transactions, biological traits such as genetic material, residence and geographic records, ethnicity, privacy breach and location-based service and geolocation.
Data Breach: is the intentional or unintentional release of secure records and information to an untrusted person or environment.
INFORMATION SECURITY
User Rights: is the right of a person to access certain records and information.
User Access Controls: is security that is applied to records and information that supports limiting access to “no” privileges until authorizations are in place for increase or elevation in privilege. In this way, only certain records and information are accessible by certain people.
Confidentiality: is records and information that are in strict privacy or secrecy.
Data Handling: ensures the security, confidentiality and appropriate use of all records and information stored, maintained, or transmitted by an organization, and guidelines for handling and disposal. This includes protection from unauthorized modification, destruction, or disclosure, whether intentional or accidental for information identified as personal identifying information.
Data Backups: should be a critical requirement of all organizations for all records and information backup and archive solutions. Data integrity ensures that records and information is recoverable throughout its lifecycle.
INFORMATION AUDIT
User Access: is the auditing of “who is accessing what” records and information.
Information Itself: is auditing to assure that records and information is being accessed or read has neither been tampered with, nor been altered or damaged through human or system error since the time of the last authorized access.
IT Security: is an audit on the level of information security. Within the broad scope of auditing information security, there are multiple types of audits, multiple objectives for different audits, etc. Most commonly the controls being audited can be categorized to technical, physical and administrative. Auditing information security covers topics from auditing the physical security of data centers to auditing the logical security of databases and highlights key components to look for and different methods for auditing these areas.
E-MAIL MANAGEMENT
Organization Policy: is policy that an organization implements for the acceptable usage of its e-mail system.
Usage Rules: are rules installed by an organization that dictates user behavior for e-mail usage.
Retention & Disposition: see “Records Management” Retention & Disposition.
Disposal Policy: see “Records Management” Disposal Policy.
Archive: see “Records Management” Archive.
TRAINING
Information Governance (IG) training is critical so that organization staff members acquire knowledge, skills, and competencies to perform records and information management job functions. IG training has specific goals of improving staff member capabilities, capacities, productivity and performance in managing records and information.
BST provides a wide variety of solutions for IG whether an organization wants to reduce the risk of litigation, cut back on the use of paper, or utilize the latest digital imaging technologies for "info-efficiency."
Information Governance Holistic Apporach Dynamics
Holism is the idea that systems (Records and Information, Information Governance, Information Technology, organizations, or any other "system") and their properties should be viewed as wholes and not as collections of parts. This often includes the view that systems function as wholes and that their functioning cannot be fully understood solely in terms of their component parts. For example, in branding, a "holistic brand" is considering the entire brand or image of the organization.
Holistic Approach Dynamics (HAD) is a concept that was developed by BST and is utilized to implement an organization's information solution whether it is the deployment of an efficiency application such as a document/records solution, or the design and development of a website that promotes an organization's information solution. In either case, the end result is an overall "attainable information solution."
Information Governance Holistic Approach Dynamics (HAD) Concept
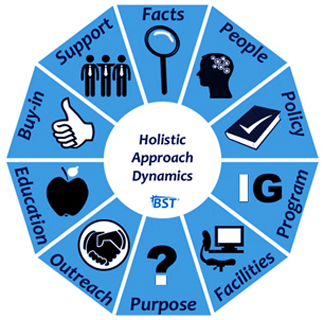
Information Governance Holistic Approach Dynamics (HAD) Breakdown

-
Information is an asset
-
Information has purpose
-
Information has sources & targets
-
Information has deadlines
-
Information has consumers
-
Information carries obligations
-
Information carries risks
-
Information has many forms
-
Information isn't immortal
-
Information demands accountability

In forward-thinking organizations, an Information Governance Manager (IGM) should be on the organizational chart in a solidified position. The IGM should also a part of the executive level interactions. The IGM “is the authority on the lifecycle of records and information” which includes understanding where it resides, records retention and disposition policies, and archival procedures. The IGM provides the leadership and a framework for an organization to be assured that information processes are appropriately secure and legal.
At first glance it may seem like the most expedient approach to information is for the IGM to create the records and information policies based on his/her knowledge of laws and regulations and then just communicate these rules out to the organization. This has an appealing simplicity but it ignores some basic realities. Information touches virtually every function within the organization and a failure to understand the needs of various organization personnel can ultimately derail the success of an information program. In all organizations there is an IT department, business units, legal departments, and records and information is stored in multiple systems and datacenters. Laws and regulations are always changing so the input of legal counsel is vital. The best approach is to make sure that the relevant stakeholders are included in the process from the early stages. This requires the need for an "Information Governance Steering Committee."

The foundation of any information program should always be in the form of a solid, comprehensive Records and Information Management (RIM) policy. It is fundamentally important for organizations to develop information policy for a variety for reasons including compliance, risk of audit and knowledge for personnel to form educated attitudes about information. An organization without information policy is an organization without information control. If there are no formal documented policies, then organization personnel at any level have no guidance on how to make information decisions.

Information Governance (IG) is the set of multi‐disciplinary structures, policies, procedures, processes and controls implemented to manage records and information at an enterprise level, supporting an organization's immediate and future regulatory, legal, risk, environmental and operational requirements. Information Technology (IT) is the application of computers and telecommunications equipment to store, retrieve, transmit and manipulate data, often in the context of a business or other enterprise. It makes sense to be separate IG from IT and have IG as a standalone program. The objectives of IG and IT are not the same in most ways. IG agendas and business processes are very different from IT. IG should be a customer of IT much like HR or Finance, etc. Support of backend infrastructure is on IT – servers, databases, etc. Development of information policy, support of frontend components such as the applications, scanners, etc., and direct personnel support is on IG.

-
A dedicated office area where a records and information program is managed and policy is developed. It also is a location to stage documents for preparation for scanning, sorting, classifying or archival determination.
-
Adequate areas for the storage of physical records whether it is onsite or at an offsite location - these areas can be secure.
-
A secure area where Information Technology infrastructure exits and houses servers and storage area networks. The servers house databases and applications that are the backend of an electronic document management system and storage area networks house digital information.

Information goals are general guidelines that explain how organizations manage and govern information. They are usually long-term and represent visions. Information objectives define strategies or implementation steps to attain the identified goals. Unlike goals, objectives are specific, measurable, and have a defined completion date. They are more specific and outline the “who, what, when, where, and how” of reaching information goals.

Outreach is an organization’s active involvement in providing their personnel with knowledge of records and information management. It also teaches and promotes overall best practices.

Not everyone in the organization is a records and information professional but all personnel should have knowledge of basic information management fundamentals. Sometimes information managers and end users don’t speak the same language, and it’s sometimes difficult for information managers to break down technical topics in a way users can understand. Educating users is essential so that all of organization's personnel are on the same page when it comes to information management.

Buy‐in is the acceptance of, and commitment to a specific concept or course of action. Buy‐in is used in the context of an organization's "people" agreeing to accept something and provide their support of information programs.

Executive Management Support is when an organization's high level managers support the endeavors of records and information management in the organization.
1. Information is an organizational asset:
In the course of our careers, we produce and receive information. It doesn’t belong to us, it belongs to the organization. As such, we need to treat it like any other organizational asset. Even if you use a personal device to produce the information, it still belongs to the organization. Assets have acquisition costs, maintenance costs, residual value (sometimes), and get disposed of at the end of their useful lives. This very much applies to information also.
2. Understand what you’re using information for:
How does information help organizations achieve strategic objectives? A government entity and a direct‐to‐consumer sales organization may use some of the same information, but they will use it differently and for different purposes. Understanding what you’re using information for helps organizations understand what information they actually need.
3. Understand where information is coming from and where it’s going to:
Information doesn’t magically appear; it comes from somewhere - someone. Organizations need to identify their internal and external information sources. Most organizations don’t just create information ad hoc. Information is intended for specific audiences and for specific purposes. Organizations need to understand what effect their information is intended to have, and who wants or needs it.
4. Understand when you need information:
Information is needed at various points in the business and decision making processes. Is real-time information really necessary or can you wait a few minutes or hours for it? Figure out when information is actually needed in order to make a decision.
5. Understand who can and should be using information, and for what:
This is not just about security, though that’s a big piece. This is also about getting the information out to those who need it or to those that organizations want to influence with it. Once the information has found its way to the audience, what are they going to do with it? Are they going to make a decision, buy something, receive a benefit…?
6. Understand your social, regulatory, and compliance obligations:
Depending on what you do and for whom you do it, you have information related obligations. Some of these are imposed by statute, some by convention, and some are self‐imposed. These obligations determine how long you must keep information, what you can do with it at the end of its life cycle, and to whom you may or must disclose it when asked.
7. Understand information related risks (too much, not enough, disclosure, etc.):
-
If some organization information leaks, what’re the consequences and can you live with them?
-
If organizations are overwhelmed by information how does it impact performance?
-
If organizations are missing information can they still get things done?
-
How likely is the organization to be sued?
8. Understand how stakeholders are interacting with information It’s not enough to know what an organization's stakeholders are doing with information. Organizations need to figure out how they’re doing it. It’s not enough to identify the types and locations of devices that stakeholders are using; organizations also need to find out if the interactions are passive or active.
9. With few exceptions, information has a finite useful life:
Unless an organization's information has historical/archival/archeological value, get rid of it as soon as you can. It’s not just about the whole discovery/litigation thing; it’s also about de-cluttering and being info‐efficient. Information is a perishable good; once it’s stale or rotted, get rid of it.
10. Make someone accountable for information:
Overall organizational performance, financial performance, legal, technology … they all have single-role accountability and responsibility. As, arguably, the second most important asset of an organization, information deserves at least the same level of attention as finance, IT, HR, legal, etc. A C-level executive needs to be accountable for how information is governed and managed across the organization.